Basically Dynamic Multipoint VPN or DMVPN is a method of building dynamically secure overlay networks on top of an unsecured medium such as the Internet. There are of course Pros and Cons when it comes to building networks across the Internet. A couple of major Cons would be the lake of SLA’s that are inherent over a private MPLS, and the second would be the overhead involved securing such a network. In a true production implementation of DMVPN you’re going to want to encrypt or protect the traffic traversing the GRE Tunnel’s, but for this example I’m going to focus primarily on getting DMVPN up and running along with covering Next Hop Resolution Protocol or NHRP. I’ll provide a follow-up post with the same topology utilizing IPSEC over the GRE Tunnels. The coolest thing is the ability for the Spoke Routers to check in with the Hub Router, and build dynamic tunnels from Spoke to Spoke without the need to the traffic to traverse back through the Hub.
NHRP
The Next Hop Resolution Protocol is an ARP like protocol that alleviates NBMA network problems. With Next Hop Resolution Protocol, systems attached to an NBMA network dynamically learn the NBMA address of the other systems that are part of that network allowing these systems to directly communicate without requiring traffic to use an intermediate hop. Basically NHRP facilitates the mapping or resolution shortcoming in a traditional NBMA network. You can think of being somewhat like ARP except that we’re not mapping Layer 3 to Layer 2, but Layer 3 to Layer 3.
GRE Overhead
As I mentioned above I’m not configuring IPSEC over GRE in this example, but regardless their is still added overhead involved. With the added need The smaller MTU allows room for IPsec and GRE overhead, without exceeding the 1500 and causing additional fragmentation.
MTU vs MSS
The Maximum Transmission Unit or MTU is the maximum length of an Ethernet frame on a given interface. This is the Frame minus the Ethernet header and trailer. In most cases the MTU is 1500 bytes in length. The Payload or MSS is the portion or Packet inside the Frame minus the Layer 3 IP header, and Layer 4 TCP Header. For example lets say we have a Packet with a 20 byte IP header + 20 byte TCP header, that would leave use with an MSS size of 1460 bytes.
Distance Vector
I’m using EIGRP in this example which is a distance vector routing protocol, and by design has Split Horizon enabled. So to overcome this limitation on the Hub we need to make sure that it can advertise routes it’s learned back out the same Tunnel interface. This is only necessary on the Hub since it’s acting as the NHS Server.
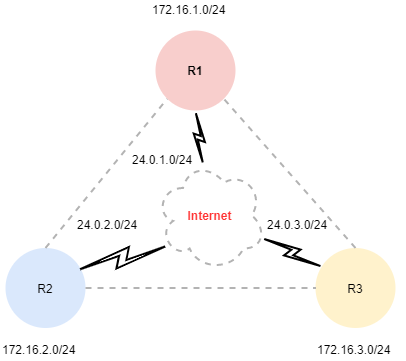
Let’s get started by bringing up the serial WAN global outside interface on the Hub Router R1.
R1#configure termianl R1(config)#interface serial0/0 R1(config-if)#ip address 24.0.1.2 255.255.255.252 R1(config-if)#no shutdown R1(config-if)#exit R1(config)#
Because we’re not running BGP with Service Provider we need create a static default route for the outside global address on Router R1 pointed at the cloud. This would be typical on a Customer edge Router that’s not exchanging public routes.
R1#configure terminal R1(config)#ip route 0.0.0.0 0.0.0.0 24.0.1.1 R1(config)#
Next lets bring up the Loopback interface that we will advertise via EIGRP from Router R2.
R1(config)#interface loopback 0 R1(config-if)#ip address 172.16.1.1 255.255.255.0 R1(config-if)#exit R1(config)#
As I mentioned above the Hub needs to advertise those routes which its learned back out the same Tunnel interface they arrived on, so we need to make sure to disable a couple of Distance Victor routing protocol features. The first being Split Horizon, and the other Next Hop Self. I’m also utilizing a very simple authentication password of dmvpn, but you can use anything that you want.
R1(config)#interface tunnel 0
R1(config-if)#ip address 10.0.0.1 255.255.255.0
R1(config-if)#no ip split-horizon eigrp 1 - - - Advertise distance vector back out Tunnel it learned from
R1(config-if)#no ip next-hop-self eigrp 1 - - - Don't modify the Tunnel next hop
R1(config-if)#ip nhrp authentication dmvpn
R1(config-if)#ip nhrp map multicast dynamic
R1(config-if)#ip nhrp network-id 1
R1(config-if)#tunnel source Serial0/0
R1(config-if)#tunnel mode gre multipoint
R1(config-if)#tunnel key 1
R1(config)#exit
R1(config)#
Now lets get EIGRP up and running on the Hub Router
R1(config)#router eigrp 1 R1(config-router)#network 10.0.0.0 R1(config-router)#network 172.16.1.0 0.0.0.255 R1(config-router)#no auto-summary R1(config-router)#end R1#
Next will configure the outside global address on Router R2.
R2#configure terminal R2(config)#interface serial0/0 R2(config-if)#ip address 24.0.2.2 255.255.255.252 R2(config-if)#no shutdown R2(config-if)#exit R2(config)#
Just as we did on router R1 lets add the static default router on router R2 to the Service Provider cloud.
R2#configure terminal R2(config)#ip route 0.0.0.0 0.0.0.0 24.0.2.1 R2(config)#
Next lets bring up a loopback interface on Router R2 that we can advertise via EIGRP.
R2(config)#interface loopback 0 R2(config-if)#ip address 172.16.2.1 255.255.255.0 R2(config-if)#exit R2(config)#
Now that we have both interfaces configured lets move onto EIGRP.
R2(config)#router eigrp 1 R2(config-router)#network 10.0.0.0 R2(config-router)#network 172.16.2.0 0.0.0.255 R2(config-router)#no auto-summary R2(config-router)#exit R2(config)#
Now lets get the Tunnel interface up and running on R2. I need to make sure that I use the same authentication password of dmpvn that I defined on the Hub router. The GRE type needs to be multipoint, and mapping needs to be pointed at the Hub.
R2(config)#interface tunnel 0
R2(config-if)#ip address 10.0.0.2 255.255.255.0
R2(config-if)#ip nhrp authentication dmvpn
R2(config-if)#ip nhrp map multicast 24.0.1.2
R2(config-if)#ip nhrp map 10.0.0.1 24.0.1.2 - - - Map GRE address to Outside Global address
R2(config-if)#ip nhrp network-id 1
R2(config-if)#ip nhrp nhs 10.0.0.1
R2(config-if)#tunnel source serial0/0
R2(config-if)#tunnel mode gre multipoint
R2(config-if)#tunnel key 1
R2(config-if)#end
R2#
Just like we did on Router R2 lets bring up the global address on router R3.
R3#configure terminal R3(config)#interface Serial0/0 R3(config-if)#ip address 24.0.3.2 255.255.255.252 R3(config-if)#no shutdown R3(config-if)#exit R3(config)#
Next lets add the necessary outside global default static route to the Service Provider cloud on Router R3
R3#configure terminal R3(config)#ip route 0.0.0.0 0.0.0.0 24.0.3.1 R3(config)#
Just as we did on Router R2 lets bring up a loopback interface that we can advertise via EIGRP.
R3(config)#interface loopback 0 R3(config-if)#ip address 172.16.3.1 255.255.255.0 R3(config-if)#exit R3(config)#
Just like with the Hub Router R1 we need to we need to bring up EIGRP on spoke Router R2.
R3(config)#router eigrp 1 R3(config-if)#network 10.0.0.0 R3(config-if)#network 172.16.3.0 0.0.0.255 R3(config-if)#no auto-summary R3(config-if)#exit R3(config)#
Lets finish thing up with bringing the Tunnel interface on router R3.
R3(config)#interface tunnel 0
R3(config-if)#ip address 10.0.0.3 255.255.255.0
R3(config-if)#ip nhrp authentication dmvpn
R3(config-if)#ip nhrp map multicast 24.0.1.2
R3(config-if)#ip nhrp map 10.0.0.1 24.0.1.2 - - - Map GRE address to Outside Global address
R3(config-if)#ip nhrp network-id 1
R3(config-if)#ip nhrp nhs 10.0.0.1
R3(config-if)#tunnel source serial0/0
R3(config-if)#tunnel mode gre multipoint
R3(config-if)#tunnel key 1
R3(config-if)#end
R3#
Helpful Commands
- show ip nhrp
- clear ip nhrp
- clear ip nhrp [ address ]
- show dmvpn
I hope you found this post on DMVPN helpful and informative. Be sure to let me know what you think by leaving suggestions, and feedback in the comments section below. You can find out more about these and other articles be checking out recent posts and archives. To learn more about me be sure to check out the About page. And as always thanks again for visiting The Packet.
