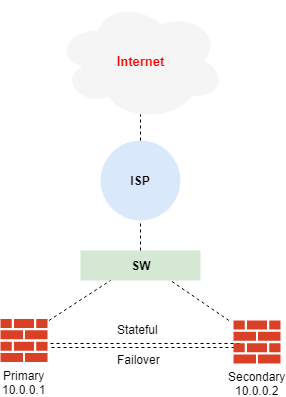
The ASA failover configuration or HA requires that both units be identical and connected to each other through a dedicated link, and optionally a Stateful link. The overall health of the active interfaces and units is monitored to determine if specific failover conditions are met.
Requirements
- The hardware / models must be the same
- The IOS software version must match
- The licenses features must be the same
- A dedicated or combined failover interface
- A dedicated or combined stateful interface
- Both ASAs must be in the same operational mode routed or transparent
When the units are configured for failover they are configured as either Primary or Secondary. The Primary configuration or designation is no more important then the Secondary designation. It’s merely a way of assigning membership. The unit that is actively passing traffic is considered to be the Active unit, and the unit which is not is considered the Standby unit.
ASA States
- Primary or Secondary – One not being more important then the other..!
- Active or Standby – The current state.
- The NAT translation table
- The TCP connection states
- The UDP connection states
- The active SSL VPN sessions
- The ARP table
- The Layer 2 bridge table when running in the transparent firewall mode
- The HTTP connection states IF HTTP replication is enabled
- The ISAKMP and IPSec SA table
- The GTP PDP connection database
- The routing tables
- State information for security service modules
Failover Conditions
- The Active ASA is rebooted
- A hardware failure or power failure on the active ASA
- A software failure on the active ASA
- A monitored interfaces or module fails on the active ASA
- The Standby ASA is is promoted to Active
- A speed or duplex mismatch between the Active and Standby ASA
- Environmental problem on the active ASA
If you had a need or wanted to enable HTTP failover connections so that they will survive a failover condition you can simply enable it with the following configuration command.
ASA#configure terminal ASA(config)#failover replication http ASA(config)#
The configuration of a Standby interface means that messages will be exchanged between the Active and Standby unit on that interface.This means that every interface which is configured with a Standby unit will be monitored. This also means that flow of status messages between the interfaces have to be acknowledged. That’s the whole point keeping track of all the interfaces and their status. Something else to keep in mind is your IPS modules.If you have IPS modules in your ASA and you reboot one of them and it happens to be on the Active ASA is will initiate a failover condition.
ASA#configure terminal
ASA(config)#interface Ethernet0/0
ASA(config-if)#speed 100
ASA(config-if)#duplex full
ASA(config-if)#nameif outside
ASA(config-if)#security-level 0
ASA(config-if)#ip address 12.2.3.1 255.255.255.0 standby 12.2.3.2
ASA(config-if)#end
ASA#
ASA#configure terminal
ASA(config)#interface Ethernet0/1
ASA(config-if)#speed 100
ASA(config-if)#duplex full
ASA(config-if)#nameif inside
ASA(config-if)#security-level 100
ASA(config-if)#ip address 172.16.0.4 255.255.255.0 standby 172.16.0.5
ASA(config-if)#end
ASA#
ASA#configure terminal
ASA(config)#interface Ethernet0/2
ASA(config-if)#speed 100
ASA(config-if)#duplex full
ASA(config-if)#nameif dmz
ASA(config-if)#security-level 75
ASA(config-if)#ip address 192.168.0.4 255.255.255.0 standby 192.168.0.5
ASA(config-if)#end
ASA#
ASA#configure terminal
ASA(config)#interface Ethernet0/3
ASA(config-if)#description State/Failover Interface
ASA(config-if)#speed 100
ASA(config-if)#duplex full
ASA(config-if)#no nameif
ASA(config-if)#security-level 80
ASA(config-if)#no ip address
ASA(config-if)#exit
ASA(config)#exit
ASA#
The failover configuration basically requires the following
- A dedicated or combined interface for stateful messages
- A dedicated or combined interface for failover messages
- A shared secret key between ASA’s
- A Failover IP address such as a /30 address
ASA#config t
ASA(config)#failover
ASA(config)#failover lan unit secondary
ASA(config)#failover lan interface StateFail Ethernet0/3
ASA(config)#failover key *****
ASA(config)#failover link StateFail Ethernet0/3
ASA(config)#failover interface ip StateFail 10.0.0.1 255.255.255.252 standby 10.0.0.2
ASA(config)#exit
ASA#
When two ASA’s are configured for failover they are basically identical in every way. From the Host name all they way down. The only thing that’s different is current running state of either ASA either Active vs Standby. Active unit will running with the Active IP addresses and the Standby unit is running with the Standby IP addresses.
ASA#show ip address
System IP Addresses:
Interface Name IP address Subnet mask Method
Ethernet0/0 outside 12.2.3.1 255.255.255.0 CONFIG
Ethernet0/1 inside 172.16.0.4 255.255.255.0 CONFIG
Ethernet0/2 dmz 192.168.0.4 255.255.255.0 CONFIG
Ethernet0/2 StateFail 10.0.0.1 255.255.255.252 CONFIG
System IP Addresses:
Interface Name IP address Subnet mask Method
Ethernet0/0 outside 12.2.3.1 255.255.255.0 CONFIG
Ethernet0/1 inside 172.16.0.4 255.255.255.0 CONFIG
Ethernet0/2 dmz 192.168.0.4 255.255.255.0 CONFIG
Ethernet0/2 StateFail 10.0.0.1 255.255.255.252 CONFIG
Lets take a look at the Interfaces on the Standby ASA. You can clearly see that the Standby ASA in the lower section has the standby IP address assigned. The assignment of these will flip when Active ASA fails over to the standby role.
ASA#show ip address
System IP Addresses:
Interface Name IP address Subnet mask Method
Ethernet0/0 outside 12.2.3.1 255.255.255.0 CONFIG
Ethernet0/1 inside 172.16.0.4 255.255.255.0 CONFIG
Ethernet0/2 dmz 192.168.0.4 255.255.255.0 CONFIG
Ethernet0/2 StateFail 10.0.0.1 255.255.255.252 CONFIG
System IP Addresses:
Interface Name IP address Subnet mask Method
Ethernet0/0 outside 12.2.3.2 255.255.255.0 CONFIG
Ethernet0/1 inside 172.16.0.5 255.255.255.0 CONFIG
Ethernet0/2 dmz 192.168.0.5 255.255.255.0 CONFIG
Ethernet0/2 StateFail 10.0.0.2 255.255.255.252 CONFIG
