Wireshark is the world’s most popular network protocol analyzer. It lets you see what’s happening on your network at a microscopic level. It really has become the standard so to speak in the world of packet capture well at least the free World. The Wireshark development group survives thanks to the contributions of networking experts across the world.
Display Filter
Like with most products that capture data on the network you end up sifting through mountains of data that you really don’t need or want to see. WireShark offers a great way to filter out the data you don’t want to see using Display Filters. Unfortunately the Display Filters are not that straight forward and sometimes hard to understand.
WireShark comes in all the flavors from Windows, MAC, and Linux. I have run WireShark on all three OS’s, and experience is always the same it just works.
WireShark offers a comprehensive of Display Filters on their site, but I’m going to the list the one’s that I use the most often when I’m troubleshooting problems. WireShark also offers a great on line Forum where you can submit questions and get more in depth answers.
My Quick List
- Specific IP Address: ip.addr ==
- Specific Host Address: ip.host ==
- Specific Ethernet Address: eth.dst ==
- Specific Ethernet OUI Address: eth.addr[0:3] ==
- SpecifcEthernet Address: eth.addr ==
Of course a lot of what can be done with regards to display filtering simply comes down to right clicking on what your interested in looking at, but if know what you want to filter on you can just type it in.
WireShark Display Filters http://www.wireshark.org/docs/dfref
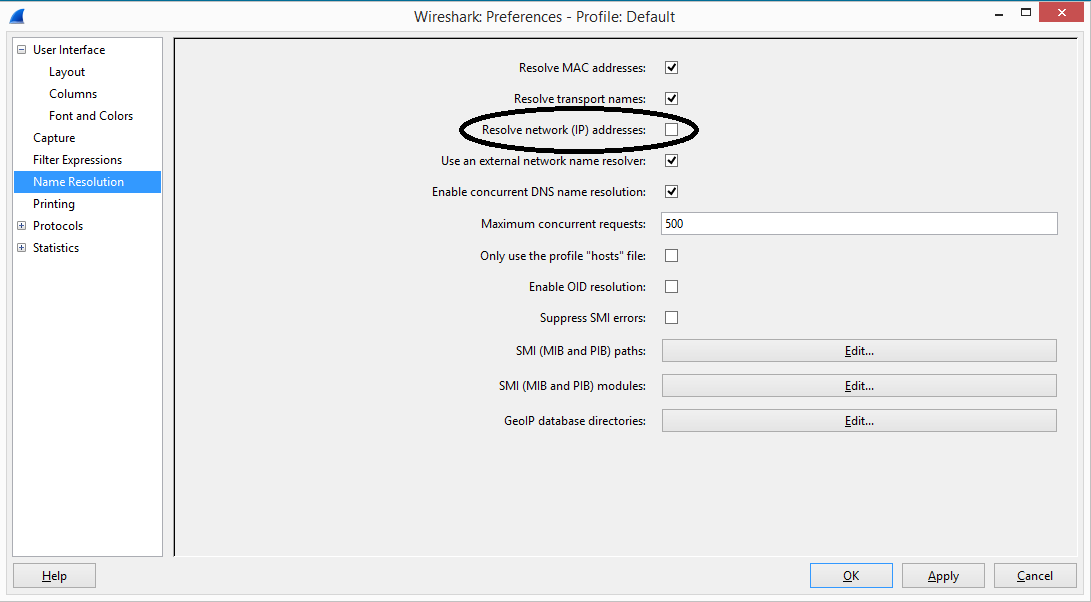
The DNS Resolution Option
There is a grate feature in WireShark for resolving DNS names that is not typically turned on by default. This is a vary useful feature when troubleshooting specific Host related issues.
From the Main menu simply select Edit
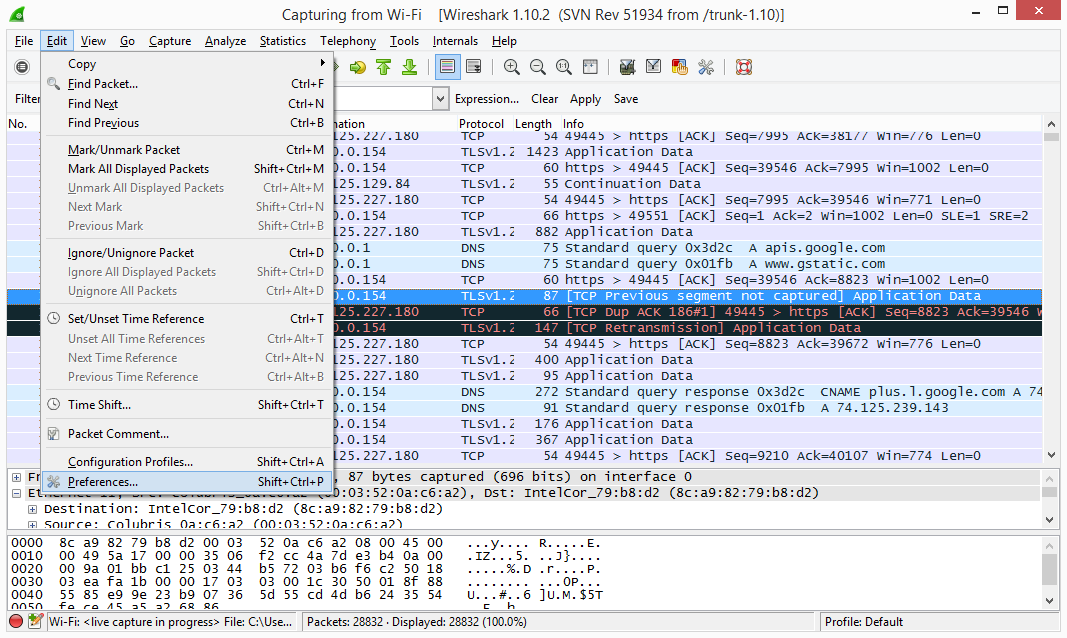
From the Edit Menu select Preferences and navigate down to Name Resolution.
Performing Remote Captures
WireShark has the capability of performing remotes captures across the network via the remote interface feature. Basically this allows you to setup a specifc Host or Hosts that you want to capture traffic on without loading WireShark on each one. There is some setup involved on the remote Host or Hosts that you want to capture traffic on. For Windows Hosts
In order to Capture Traffic on a remote Windows Host or Hosts the target machine must be running the WinPcap Service. WinPcap is actually one of the foundation pieces of WireShark The easiest way is to install just WinPcap alone is to simply download it from the WinPcap website.After the installation is completed go to the Services control panel, find the Remote Packet Capture Protocol service and start it.
- WinPcap http://www.winpcap.org
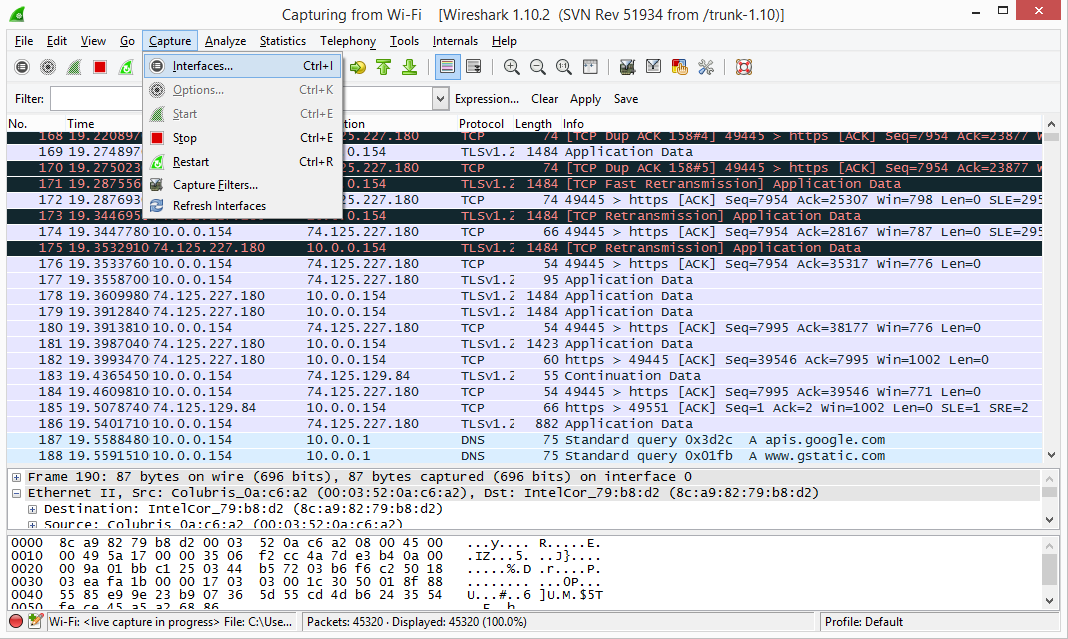
Once you have the WinPcap Service up and running on the target Host or Hosts you need to add the remote Interface option on your WireShark Client. Simply select Capture from the Main menu and select Interfaces.
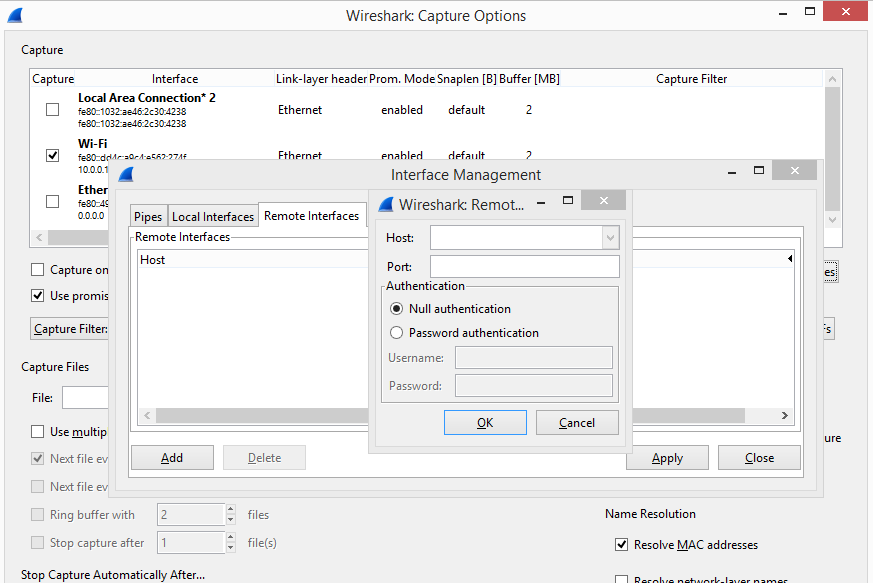
From the Interfaces window click on the Options button and then select the Manage Interfaces from the next window.
From the Manage Interfaces options select Remote Interfaces Tab and click on Add. From hear you can specify the remote Host and port you want to connect to.
There is tons, and tons of information out there regarding WireShark. It’s a great tool and its complete free.! If your new to WireShark I would recommend using the on-line forms along with the Help documentation that comes with WireShark. I would also highly recommend checking out Chris Greer’s YouTube channel Chris Greer’s YouTube Channel it’s full of some great videos around troubleshooting with WireShark.
WireShark Ask A Question http://ask.wireshark.org
