IPSEC functionality provides network data encryption at the IP packet level or Layer 3 hence the word IP in IPsec. IPSEC offers a robust security solution that is standards-based. IPSEC provides data authentication and anti-replay services in addition to data confidentiality services. IPSEC is the only way to implement secure Virtual Private Networks or VPNs.
A while back I had the opportunity to convert our B2B IPSEC Tunnels from an old Cisco 3005 Concentrator over to the ASA. Honestly I couldn’t wait to get off the 3005 for two reasons. The first was because I wanted the IPSEC Tunnels terminating on the ASA and the other was due to instability we were experiencing with the 3005. We were constantly having to reset the connections almost on a daily basis. I recently had the opportunity to set up a Tunnel with multiple security association for an acquisition where we needed to bring the two Company networks together during the transition phase.
I have 4 ASA Firewalls in my environment at two different Datacenters. Two of the ASA’s are 5510’s and the other Datacenter has two 5520’s. Both Datacenters are running in a Primary / Standby configurations on version 8.4.
ISAKMP Encryption
- DES 56-bit
- 3DES 168-bit
- AES 128-bit
- AES 192-bit
- AES 256-bit
ISAKMP Hashing
- MD5
- SHA
ISAKMP Authentication
- Preshared keys
- RSA signature
- DSA signature
ISAKMP DH Groups
- Group 1 768-bit field
- Group 2 1024-bit field
- Group 5 1536-bit field
- Group 7 ECC 163-bit field
ISAKMP Lifetime
- 120–2,147,483,647 seconds
IPSEC Authentication
- None
- DES 56-bit
- 3DES 168-bit
- AES 128-bit
- AES 192-bit
- AES 256-bit
IPSEC Hashing
- MD5
- SHA
- None
IPSEC Modes
- Tunnel
- Transport
IPSEC Lifetime
- 120–2,147,483,647 seconds
- 10–2,147,483,647 KB
Transform Set Encryption
- esp-3des
- esp-aes
- esp-aes-192
- esp-aes-256
- esp-des
- esp-null
Transform Set Hashing
- esp-md5-hmac
- esp-sha-hmac
- esp-none
The Phases of IPSEC Encryption
IKE Phase 1
- Authenticates and protects the identities of the IPSec peers
- Negotiates a matching IKE SA policy between peers to protect the IKE exchange
- Performs Authenticated Diffie-Hellman exchange shared secret keys
- Sets up a secure tunnel to negotiate IKE phase 2 parameters
IKE Phase 2
- Negotiates IPSec SA parameters protected by an existing IKE SA
- Establishes IPSec security associations
- Periodically renegotiates IPSec SAs to ensure security
- Optionally performs an additional Diffie-Hellman exchange
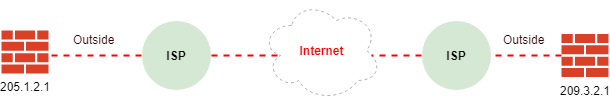
Example Configuration

- Company A: ASA-A Public IP = 205.1.2.1
- Company A: Networks: 172.16.1.0, and 172.16.2.0
- Company B: ASA-B Public IP = 209.3.2.1
- Company B: Networks: 192.168.1.0, and 192.168.2.0
I always use Objects along with Object Groups when I can. That is one of the reach features of the ASA Firewall IOS the ability to nest Objects within Object Groups. Because this example is based on Networks and not Hosts, I’m going to use Objects Groups. You can define an object of type network with a subnet range, but it has to be a contiguous range.
Configure the Outside Public Interfaces on ASA-A
ASA-A#config t
ASA-A(config)#interface GigabitEthernet0/0
ASA-A(config-if)#speed 100
ASA-A(config-if)#duplex full
ASA-A(config-if)#nameif outside
ASA-A(config-if)#security-level 0
ASA-A(config-if)#ip address 205.1.2.1 255.255.255.240 standby 205.1.2.2
ASA-A(config-if)#exit
ASA-A#
The Object Group on ASA-A used for interesting traffic with Company A
ASA-A#config t
ASA-A(config)#object-group network A
ASA-A(config-network-object)#network-object 172.16.1.0 255.255.255.0
ASA-A(config-network-object)#network-object 172.16.2.0 255.255.255.0
ASA-A(config-network-object)#exit
ASA-A(config)#exit
ASA-A#
The Object Group on ASA-A used for interesting traffic with Company B
ASA-A#config t
ASA-A(config)#object-group network B
ASA-A(config-network-object)#network-object 192.168.1.0 255.255.255.0
ASA-A(config-network-object)#network-object 192.168.2.0 255.255.255.0
ASA-A(config-network-object)#exit
ASA-A(config)#exit
ASA-A#
Add the static routes on ASA-A for the networks on ASA-B
ASA-A#config t
ASA-A(config)#ip route outside 192.168.1.0 255.255.255.0 205.1.2.1
ASA-A(config)#ip route outside 192.168.2.0 255.255.255.0 205.1.2.1
ASA-A(config)#exit
ASA-A#
Add the NAT exemption on ASA-A between A and B
ASA-A#config t
ASA-A(config)#nat (inside,outside) source static A A destination static B B no-proxy-arp
ASA(config)#exit
ASA-A#
ASA-A#config t
ASA-A(config)# crypto ikev1 policy 1
ASA-A(config)# authentication pre-share
ASA-A(config)# encryption 3des
ASA-A(config)# hash sha
ASA-A(config)# group 2
ASA-A(config)# lifetime 86400
ASA-A(config)#exit
ASA-A#
ASA-A#config t
ASA-A(config)#crypto ipsec ikev1 transform-set B esp-3des esp-md5-hmac
ASA-A(config)#exit
ASA-A#
ASA-A#config t
ASA-A(config)#tunnel-group 209.3.2.1 type ipsec-l2l
ASA-A(config)#tunnel-group 209.3.2.1 ipsec-attributes
ASA-A(config)#ikv1 pre-shared-key *****
ASA-A(config)#exit
ASA-A#
I always like to call or name the crypto map something short and simple. So I always use the word VPN, but you can use any thing that makes sense to you. The crypto map name can be used over and over with other crypto maps.
ASA-A#config t
ASA-A(config)#crypto map VPN 1 match address B
ASA-A(config)#crypto map VPN 1 set pfs
ASA-A(config)#crypto map VPN 1 set peer 209.3.2.1
ASA-A(config)#crypto map VPN 1 set ikev1 transform-set B
ASA-A(config)#crypto map VPN interface outside
ASA-A(config)#exit
ASA-A#
Configure the ACL used for interesting traffic sourced from ASA-A
ASA-A#config t
ASA-A(config)#access-list B permit ip object-group A object-group B
ASA(config)#exit
ASA-A#
Enable the IPSEC Tunnel on the outside public interface
ASA-A#crypto ikev1 enable outside
Lets take a look at the object NAT between A and B
ASA-A#show nat object-group A
Manual NAT Policies (Section 1)
6 (inside) to (outside) source static A A destination static B B no-proxy-arp
translate_hits = 142, untranslate_hits = 396
ASA-A#show nat object-group B
Manual NAT Policies (Section 1)
6 (inside) to (outside) source static A A destination static B B no-proxy-arp
translate_hits = 137, untranslate_hits = 420
ASA-A#show crypto ipsec sa summary
Current IPSec SA's: Peak IPSec SA's:
IPSec : 21 Peak Concurrent SA : 62
IPSec over UDP : 0 Peak Concurrent L2L : 62
IPSec over NAT-T : 0 Peak Concurrent RA : 0
IPSec over TCP : 0
IPSec VPN LB : 0
Total : 21
Configure the Outside Public Interface on ASA-B
ASA-B#config t
ASA-B(config)#interface GigabitEthernet0/0
ASA-B(config-if)#speed 100
ASA-B(config-if)#duplex full
ASA-B(config-if)#nameif outside
ASA-B(config-if)#security-level 0
ASA-B(config-if)#ip address 209.3.2.1 255.255.255.240 standby 209.3.2.2
ASA-B(config)#exit
ASA-B#
Configure the Object Group on ASA-B to define interesting traffic for Company A
ASA-B#config t
ASA-B(config)#object-group network A
ASA-B(config-network-object)#network-object 172.16.1.0 255.255.255.0
ASA-B(config-network-object)#network-object 172.16.2.0 255.255.255.0
ASA-B(config-network-object)#exit
ASA-B(config)#exit
ASA-B#
Configure the Object Group on ASA-B to define interesting traffic for Company B
ASA-B#config t
ASA-B(config)#object-group network B
ASA-B(config-network-object)#network-object 192.168.1.0 255.255.255.0
ASA-B(config-network-object)#network-object 192.168.2.0 255.255.255.0
ASA-B(config-network-object)#exit
ASA-B(config)#exit
ASA-B#
Add the static routes on ASA-A for the networks on ASA-B
ASA-B#config t
ASA-B(config)#ip route outside 172.16.1.0 255.255.255.0 205.1.2.3
ASA-B(config)#ip route outside 192.16.2.0 255.255.255.0 205.1.2.3
ASA-B(config)#exit
ASA-B#
Add the static NAT exemption on ASA-B between B and B
ASA-B#config t
ASA-B(config)#nat (inside,outside) source static B B destination static A A no-proxy-arp
ASA-B(config)#exit
ASA-B#
ASA-B#config t
ASA-B(config)#crypto ikev1 policy 1
ASA-B(config)#authentication pre-share
ASA-B(config)#encryption 3des
ASA-B(config)#hash sha
ASA-B(config)#group 2
ASA-B(config)#lifetime 86400
ASA-B(config)#exit
ASA-B#
ASA-B#config t
ASA-B(config)#crypto ipsec ikev1 transform-set A esp-3des esp-md5-hmac
ASA-B(config)#exit
ASA-B#
ASA-B#config t
ASA-B(config)#tunnel-group 209.1.2.1 type ipsec-l2l
ASA-B(config)#tunnel-group 209.1.2.1 ipsec-attributes
ASA-B(config)#ikv1 pre-shared-key *****
ASA-B(config)#exit
ASA-B#
I always like to call or name the crypto map something short and simple. So I always use the word VPN, but you can use any thing that makes sense to you. The crypto map name can be used over and over with other crypto maps.
ASA-B#config t
ASA-B(config)#crypto map VPN 1 match address A
ASA-B(config)#crypto map VPN 1 set pfs
ASA-B(config)#crypto map VPN 1 set peer 209.1.2.1
ASA-B(config)#crypto map VPN 1 set ikev1 transform-set A
ASA-B(config)#crypto map VPN interface outside
ASA-B(config)#exit
ASA-B#
Configure the ACL used for interesting traffic sourced from ASA-B
ASA-B#config t
ASA-B(config)#access-list A permit ip object-group B object-group A
ASA-B(config)#exit
ASA-B#
Enable the IPSEC Tunnel on the outside public interface
ASA-B#crypto ikev1 enable outside
Lets take a look at the object NAT between A and B
ASA-B#show nat object-group A
Manual NAT Policies (Section 1)
6 (inside) to (outside) source static A A destination static B B no-proxy-arp
translate_hits = 142, untranslate_hits = 396
ASA-B# show nat object-group B
Manual NAT Policies (Section 1)
6 (inside) to (outside) source static A A destination static B B no-proxy-arp
translate_hits = 137, untranslate_hits = 420
ASA-B#show crypto ipsec sa summary Current IPSec SA's: Peak IPSec SA's: IPSec : 21 Peak Concurrent SA : 62 IPSec over UDP : 0 Peak Concurrent L2L : 62 IPSec over NAT-T : 0 Peak Concurrent RA : 0 IPSec over TCP : 0 IPSec VPN LB : 0 Total : 21
